- Security: fugitive and wealthy: life on the run from the biggest cyberstaffler in Spain
- Security: Of hacker sentenced to direct the security of Telefónica
When FBI agents pounded on Reality Leigh Winner's door, they were going for a shot. They knew he was guilty. Her printer would take her to spend the next five years of her life behind bars.
They had spent the past two days cautiously inspecting an internal NSA document that someone had leaked to the press. This document spoke about the efforts that Russia had undertaken to influence the United States presidential elections days before the information.
The person who leaked the intelligence information tried to be cautious. She sought to avoid leaving a digital trail or metadata that could place it as the source of the news. To do this, she printed the documents and sent them by ordinary mail. A document that, for security reasons, had previously censored parts.
The Intercept, the outlet that published the story, scanned the printed reports it had received and attached them to the story to add documentary value to the information.
Without knowing it, her source had been sold and exposed because those papers contained all the information that gave her away as the source of the news. But how had it happened?
The case fell into the hands of the FBI (the United States security corps in charge of counterintelligence tasks in national territory) and the agents, as in the famous graduation speech delivered by Steve Jobs, only had to connect the dots to know who was behind .
So, 48 hours after the news was published, they went to Reality Leigh Winner's house knowing that she was the source that had leaked the intelligence. After spending several years in military intelligence for the United States Air Force, the young woman had used her level of access credentials while working as a contractor at a private security company to get the document, distribute it, and pass it on to the press. Her printer gave her away .
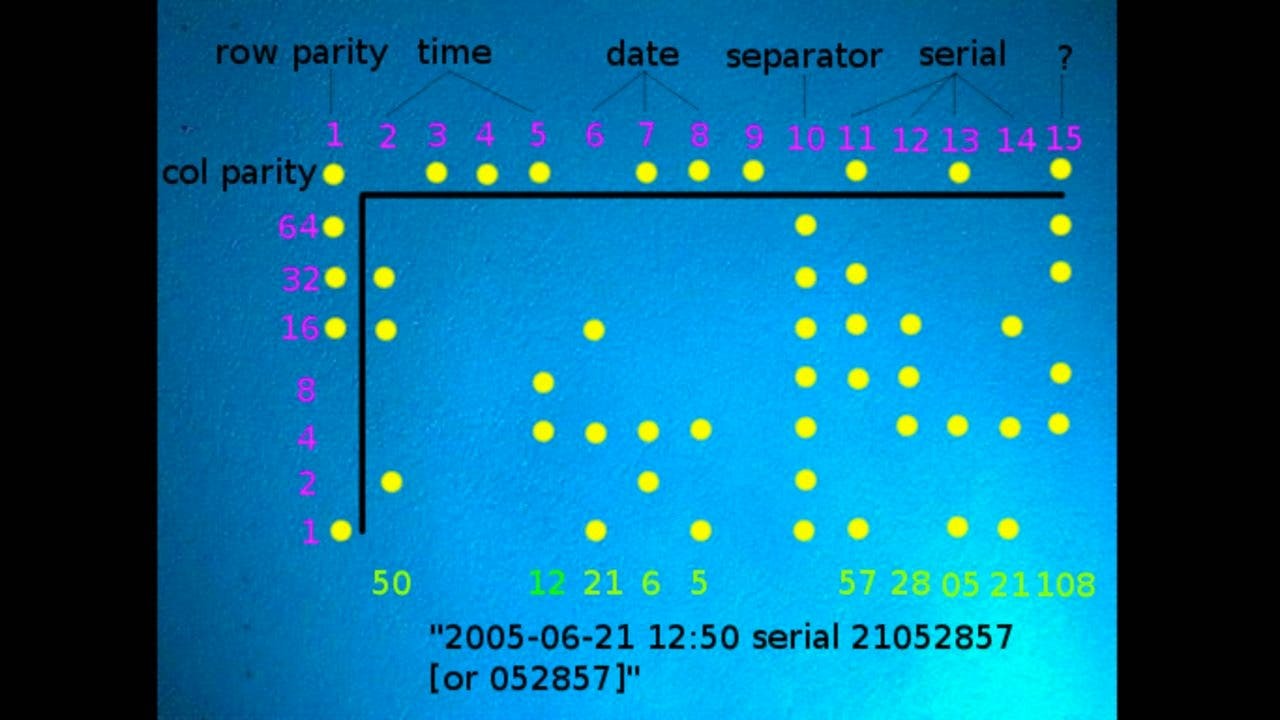
Once detained, the woman quickly confessed to the events. The FBI didn't have to put too much pressure on her because the tests were overwhelming because of the watermark in the form of microscopic yellow dots left by her printer.
After pleading guilty to a crime of " transmitting information concerning national defense ", he reached an agreement with the prosecution and accepted a sentence of 5 years and three months in prison.
Microscopic yellow dots and other hidden watermarks left by printers
The vast majority of printers contain hidden watermarks in the form of yellow dots (virtually invisible to the human eye) that form a coded pattern. Said pattern (usually located in the upper left margin -although it can be anywhere- and placed upside down with respect to how the document is read contains) information about the day, serial number, date and time when a certain document was printed .
Microdots used to give away the person who printed a document are not new. The Electronic Frontier Foundation (EFF) - a non-profit organization that fights for the respect of citizens' rights in the digital sphere - has been warning about its existence for years and, even, publishing lists of the printers in which they have detected these patterns in which the main marl of the market appear.
The EFF stopped publishing the list of printers that had or did not have yellow dots along with a warning that shows that the situation , far from improving, was getting worse.
"It seems very likely that all commercial color printers with laser technology [the standard printing technology for five years] use forensic tracking codes. Codes that yellow dots would not necessarily have to use. This is true even if those dots turn out to be Visible to the human eye or printer models are on our list. That also includes all printers that do not have the yellow dot system. "
That is, in addition to the yellow dots, the printers have other methods that allow you to leave a forensic trace . Sometimes or more difficult methods to override by hand with rudimentary techniques.
However, this physical tracking system would not be unique. Experts also warn that organizations like the NSA keep records of print orders sent by computers. Information that combined with the printer trail allows answers to questions about who, how, when and where a document was printed .
However, those who want to protect the authors of a certain document (like a journalist who wants to protect a source) can use tools like this one developed by scientists from the University of Dresden (Germany) designed to protect activists or legitimate sources of information. .
In accordance with the criteria of The Trust Project
Know more- United States
- Russia
Russian espionage The new life of the Skripal: false identity in New Zealand and a television series
Ctrl + alt + delete The best Windows Manager tricks told by its inventor
Technology Google Maps adds alerts to improve travel during de-escalation
See links of interest
- Last News
- TV programming
- English translator
- Work calendar
- Daily horoscope
- Santander League Ranking
- League calendar
- TV Movies
- Cut notes 2019
- Themes
- Seville - Real Betis