This story begins with the events of two years ago.
Then some unknown attacker "mined" the 40th Moscow hospital in Kommunarka.
According to sources in emergency services, an anonymous message about a bomb threat was sent to the e-mail of City Clinical Hospital No. 40 in the village of Kommunarka.
A few days later, planes at Sheremetyevo Airport were similarly subjected to "mining".
Similar mine threat letters were sent to many private and public institutions in the country.
At the same time, as follows from the screenshot of the message published on the official Telegram channel of the United Press Service of the Courts of St. Petersburg, the attacker demanded the return of 120 bitcoins allegedly stolen from him from the WEX cryptocurrency exchange.
Also on russian.rt.com "Confronting a feigned threat": how NATO is ramping up cyber activity near Russian borders
An essentially similar threat and a demand to return 120 bitcoins to the WEX exchange came to the city court of St. Petersburg back in November 2019.
Then the attacker revealed the number of his crypto wallet.
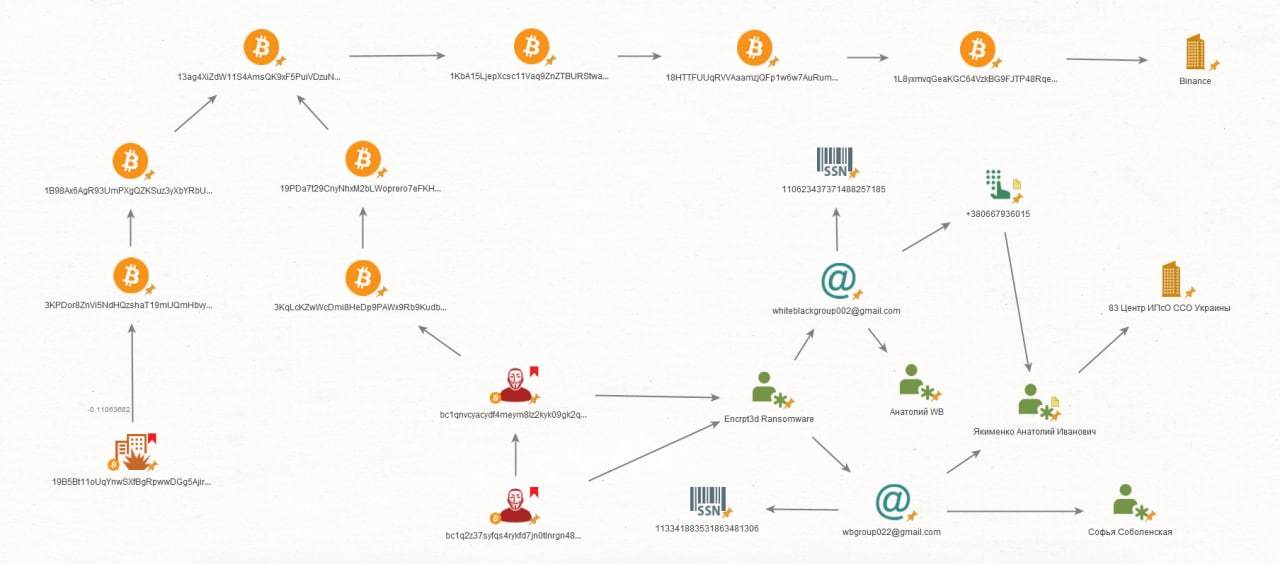
Here it is: 19B5Bt11oUqYnwSXfBgRpwwDGg5Ajirbjn.
With the help of public services, anyone can see the chain of transactions for this wallet.
Denial of the obvious
Knowing the number of the electronic wallet, T.Hunter specialists made several test payments in bitcoins in order to trace the further movement of funds.
In total, three transactions were made for a total of 0.11 BTC.
After some time, money began to be transferred from one wallet to another, which was the first thing that the head of Indefieco, Sergey Mendeleev, drew attention to.
As a result, all the funds ended up on the wallet with the number 1L8yxmvqGeaKGC64VzkBG9FJTP48RqeSct, and then they were cashed out through the well-known cryptocurrency exchange Binance.
© T.Hunter
The cashing out of the miner's funds went through the same channels as the cashing out of money from the activities of the Encrpt3d Ransomware encryption virus, which is distributed by the WhiteBlackCrypt Ransomware hacker group, experts found out.
It is a ransomware program that encrypts user data (mainly in the corporate sector) using the AES-256 algorithm.
The hackers then demand that they transfer 10 BTC to unlock and decrypt the files.
Also on russian.rt.com "Instructors behind the backs": who is behind the information attacks against Russian citizens
At the same time, as evidenced by data leaks with detailed data of groups of Ukrainian “state trolls” controlled by special services, in particular the 83rd IPSO Center, there is a connection between the pool of passwords used by Ukrainian agents in the CISO and the name of the WhiteBlackCrypt group.
It is noteworthy that the State Service for Special Communications and Information Protection of Ukraine at the beginning of the year even issued a press release in which it publicly denied the involvement of Ukrainian government agencies in the activities of the group that was spreading the encryption virus.
Not subject to liability
Attacks by hackers affiliated with the Ukrainian special services on the network infrastructure of Russia and other countries could hardly be accidental, said Vladimir Bruter, a political scientist and expert at the International Institute for Humanitarian and Political Studies, in a conversation with RT.
“The role of the Ukrainian special services in such actions is always of an auxiliary nature.
Decisions, especially in relation to Russia, are made by the political leadership, the expert noted.
“I would not discount the version that it was the hackers controlled by the Ukrainian special services who could have a side “business”, outsourcing in some way.”
The expert also noted that the activity of hackers is often a way to divert attention and disrupt the normal functioning of social services.
“The actions of hackers are usually harassing.
Systemic damage is hardly to be expected: after all, there is a reservation and everything is restored quite quickly,” the political scientist explained.
Another issue is cyber espionage.
It gives certain results."
Despite the fact that Ukrainian hackers are also active in the networks of the European Union, they are unlikely to be held accountable for their crimes, the expert believes.
“Now Ukraine and its authorities are getting away with everything, in the West there is a political consensus on this matter,” the political scientist concluded.